从几个CTF题目学习内存取证(一)
先介绍一个python写的很棒的内存取证工具--volatility,kali已经集成了,所以有kali可以直接用
┌──(root@kali)-[~]
└─# volatility --help 2 ⨯
Volatility Foundation Volatility Framework 2.6
Usage: Volatility - A memory forensics analysis platform.
Options:
-h, --help list all available options and their default values.
Default values may be set in the configuration file
(/etc/volatilityrc)
--conf-file=/root/.volatilityrc
User based configuration file
-d, --debug Debug volatility
--plugins=PLUGINS Additional plugin directories to use (colon separated)
--info Print information about all registered objects
--cache-directory=/root/.cache/volatility
Directory where cache files are stored
--cache Use caching
--tz=TZ Sets the (Olson) timezone for displaying timestamps
using pytz (if installed) or tzset
-f FILENAME, --filename=FILENAME
Filename to use when opening an image
--profile=WinXPSP2x86
Name of the profile to load (use --info to see a list
of supported profiles)
-l LOCATION, --location=LOCATION
A URN location from which to load an address space
-w, --write Enable write support
--dtb=DTB DTB Address
--shift=SHIFT Mac KASLR shift address
--output=text Output in this format (support is module specific, see
the Module Output Options below)
--output-file=OUTPUT_FILE
Write output in this file
-v, --verbose Verbose information
--physical_shift=PHYSICAL_SHIFT
Linux kernel physical shift address
--virtual_shift=VIRTUAL_SHIFT
Linux kernel virtual shift address
-g KDBG, --kdbg=KDBG Specify a KDBG virtual address (Note: for 64-bit
Windows 8 and above this is the address of
KdCopyDataBlock)
--force Force utilization of suspect profile
-k KPCR, --kpcr=KPCR Specify a specific KPCR address
--cookie=COOKIE Specify the address of nt!ObHeaderCookie (valid for
Windows 10 only)
Supported Plugin Commands:
amcache Print AmCache information
apihooks Detect API hooks in process and kernel memory
atoms Print session and window station atom tables
atomscan Pool scanner for atom tables
auditpol Prints out the Audit Policies from HKLM\SECURITY\Policy\PolAdtEv
bigpools Dump the big page pools using BigPagePoolScanner
bioskbd Reads the keyboard buffer from Real Mode memory
cachedump Dumps cached domain hashes from memory
callbacks Print system-wide notification routines
clipboard Extract the contents of the windows clipboard
cmdline Display process command-line arguments
cmdscan Extract command history by scanning for _COMMAND_HISTORY
connections Print list of open connections [Windows XP and 2003 Only]
connscan Pool scanner for tcp connections
consoles Extract command history by scanning for _CONSOLE_INFORMATION
crashinfo Dump crash-dump information
deskscan Poolscaner for tagDESKTOP (desktops)
devicetree Show device tree
dlldump Dump DLLs from a process address space
dlllist Print list of loaded dlls for each process
driverirp Driver IRP hook detection
drivermodule Associate driver objects to kernel modules
driverscan Pool scanner for driver objects
dumpcerts Dump RSA private and public SSL keys
dumpfiles Extract memory mapped and cached files
dumpregistry Dumps registry files out to disk
editbox Displays information about Edit controls. (Listbox experimental.)
envars Display process environment variables
eventhooks Print details on windows event hooks
evtlogs Extract Windows Event Logs (XP/2003 only)
filescan Pool scanner for file objects
gahti Dump the USER handle type information
gditimers Print installed GDI timers and callbacks
gdt Display Global Descriptor Table
getservicesids Get the names of services in the Registry and return Calculated SID
getsids Print the SIDs owning each process
handles Print list of open handles for each process
hashdump Dumps passwords hashes (LM/NTLM) from memory
hibinfo Dump hibernation file information
hivedump Prints out a hive
hivelist Print list of registry hives.
hivescan Pool scanner for registry hives
hpakextract Extract physical memory from an HPAK file
hpakinfo Info on an HPAK file
idt Display Interrupt Descriptor Table
iehistory Reconstruct Internet Explorer cache / history
imagecopy Copies a physical address space out as a raw DD image
imageinfo Identify information for the image
impscan Scan for calls to imported functions
joblinks Print process job link information
kdbgscan Search for and dump potential KDBG values
kpcrscan Search for and dump potential KPCR values
ldrmodules Detect unlinked DLLs
lsadump Dump (decrypted) LSA secrets from the registry
machoinfo Dump Mach-O file format information
malfind Find hidden and injected code
mbrparser Scans for and parses potential Master Boot Records (MBRs)
memdump Dump the addressable memory for a process
memmap Print the memory map
messagehooks List desktop and thread window message hooks
mftparser Scans for and parses potential MFT entries
moddump Dump a kernel driver to an executable file sample
modscan Pool scanner for kernel modules
modules Print list of loaded modules
multiscan Scan for various objects at once
mutantscan Pool scanner for mutex objects
notepad List currently displayed notepad text
objtypescan Scan for Windows object type objects
patcher Patches memory based on page scans
poolpeek Configurable pool scanner plugin
printkey Print a registry key, and its subkeys and values
privs Display process privileges
procdump Dump a process to an executable file sample
pslist Print all running processes by following the EPROCESS lists
psscan Pool scanner for process objects
pstree Print process list as a tree
psxview Find hidden processes with various process listings
qemuinfo Dump Qemu information
raw2dmp Converts a physical memory sample to a windbg crash dump
screenshot Save a pseudo-screenshot based on GDI windows
servicediff List Windows services (ala Plugx)
sessions List details on _MM_SESSION_SPACE (user logon sessions)
shellbags Prints ShellBags info
shimcache Parses the Application Compatibility Shim Cache registry key
shutdowntime Print ShutdownTime of machine from registry
sockets Print list of open sockets
sockscan Pool scanner for tcp socket objects
ssdt Display SSDT entries
strings Match physical offsets to virtual addresses (may take a while, VERY verbose)
svcscan Scan for Windows services
symlinkscan Pool scanner for symlink objects
thrdscan Pool scanner for thread objects
threads Investigate _ETHREAD and _KTHREADs
timeliner Creates a timeline from various artifacts in memory
timers Print kernel timers and associated module DPCs
truecryptmaster Recover TrueCrypt 7.1a Master Keys
truecryptpassphrase TrueCrypt Cached Passphrase Finder
truecryptsummary TrueCrypt Summary
unloadedmodules Print list of unloaded modules
userassist Print userassist registry keys and information
userhandles Dump the USER handle tables
vaddump Dumps out the vad sections to a file
vadinfo Dump the VAD info
vadtree Walk the VAD tree and display in tree format
vadwalk Walk the VAD tree
vboxinfo Dump virtualbox information
verinfo Prints out the version information from PE images
vmwareinfo Dump VMware VMSS/VMSN information
volshell Shell in the memory image
windows Print Desktop Windows (verbose details)
wintree Print Z-Order Desktop Windows Tree
wndscan Pool scanner for window stations
yarascan Scan process or kernel memory with Yara signatures具体命令如上,过多的不介绍了,根据第一个开始边做边学吧。
Memory-1
这个内存取证上半年的时候,学长就拿给我们做了,当时我和同学肝到凌晨3点,那一幕恍如昨日,熬夜肝题太爽了~
如果正常竞赛情况下,没有提示的情况下拿到文件,可以binwalk分析一下,但是这儿已经知道是内存取证了就免除了这一步。直接volatility分析:
┌──(root@kali)-[~]
└─# volatility -f memory.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (/root/桌面/memory.raw)
PAE type : PAE
DTB : 0xa8f000L
KDBG : 0x80545ce0L
Number of Processors : 1
Image Type (Service Pack) : 2
KPCR for CPU 0 : 0xffdff000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2020-05-19 10:44:24 UTC+0000
Image local date and time : 2020-05-19 18:44:24 +0800分析出来镜像的可能为WinXPSP2x86(Suggested Profile(s)显示出的),得知镜像版本后,尝试用pslist列举出内存中的进程信息。
┌──(root@Fkali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 pslist
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
-------------------------------------------------------------------------------------------------------------------
0x821bb830 System 4 0 48 250 ------ 0
0x82019da0 smss.exe 540 4 3 19 ------ 0 2020-05-19 03:59:41 UTC+0000
0x81f52550 csrss.exe 596 540 9 303 0 0 2020-05-19 03:59:44 UTC+0000
0x81f722c0 winlogon.exe 616 540 16 269 0 0 2020-05-19 03:59:48 UTC+0000
0x81f4dc08 services.exe 672 616 16 262 0 0 2020-05-19 03:59:51 UTC+0000
0x81f126e8 lsass.exe 684 616 27 335 0 0 2020-05-19 03:59:51 UTC+0000
0x81f06280 vmacthlp.exe 880 672 1 24 0 0 2020-05-19 03:59:53 UTC+0000
0x81ee4568 svchost.exe 912 672 6 104 0 0 2020-05-19 03:59:54 UTC+0000
0x81f27b28 svchost.exe 980 672 10 217 0 0 2020-05-19 03:59:54 UTC+0000
0x81ebb628 svchost.exe 1112 672 32 673 0 0 2020-05-19 03:59:55 UTC+0000
0x81ecc058 svchost.exe 1144 672 6 69 0 0 2020-05-19 03:59:55 UTC+0000
0x81ec4768 VGAuthService.e 1364 672 2 61 0 0 2020-05-19 04:00:13 UTC+0000
0x81e87760 explorer.exe 1560 1524 16 443 0 0 2020-05-19 04:00:15 UTC+0000
0x81e62880 vmtoolsd.exe 1640 672 8 234 0 0 2020-05-19 04:00:22 UTC+0000
0x81e757f8 vmtoolsd.exe 1724 1560 7 169 0 0 2020-05-19 04:00:23 UTC+0000
0x81e6a840 CTFMON.EXE 1768 1560 1 65 0 0 2020-05-19 04:00:23 UTC+0000
0x81e47b28 wmiprvse.exe 1900 912 11 228 0 0 2020-05-19 04:00:29 UTC+0000
0x81deb020 svchost.exe 1972 672 10 146 0 0 2020-05-19 04:00:30 UTC+0000
0x81de8020 WinRAR.exe 296 1560 5 202 0 0 2020-05-19 10:42:32 UTC+0000
0x81e28da0 notepad.exe 564 1560 1 46 0 0 2020-05-19 10:42:38 UTC+0000
0x81fcb878 cmd.exe 1628 1560 1 32 0 0 2020-05-19 10:42:43 UTC+0000
0x81f9e5a8 conime.exe 1740 1628 1 34 0 0 2020-05-19 10:42:43 UTC+0000
0x81df8da0 notepad.exe 688 1560 1 46 0 0 2020-05-19 10:43:51 UTC+0000
0x81fe7020 DumpIt.exe 1576 1560 1 24 0 0 2020-05-19 10:44:22 UTC+0000可以看到内存中比较引人注目的是WinRAR.exe,notepad.exe,cmd.exe,那就一个一个看,因为WinRAR.exe是压缩软件无法直接查看操作,所以先看notepad
┌──(root@kali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 notepad
Volatility Foundation Volatility Framework 2.6
Process: 564
Text:
?
Text:
d
Text:
Text:
?
Text:
key2:St3g0_
Process: 688
Text:
?
Text:
d
Text:
Text:
?
Text:
key2:St3g0_
key1:flag{7h3_
Text:
key1:flag{7h3_得到key1和key2,同时得知,这玩意儿是好(死)玩(亡)套娃...flag{7h3_St3g0_
接下来看看cmd都做了些什么
┌──(root@kali)-[~/]
└─# volatility -f memory.raw --profile=WinXPSP2x86 cmdscan
Volatility Foundation Volatility Framework 2.6
**************************************************
CommandProcess: csrss.exe Pid: 596
CommandHistory: 0x526bb8 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 3 LastAdded: 2 LastDisplayed: 2
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x410
Cmd #0 @ 0x3578fe0: wow,good job guys!
Cmd #1 @ 0x3579ed8: i will tell you the scret!
Cmd #2 @ 0x525f70: key3:1s_
**************************************************
CommandProcess: csrss.exe Pid: 596
CommandHistory: 0x529e20 Application: DumpIt.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x200好家伙,这一看历史记录就得到了key3:1s_,再看看cmd执行了那些进程
┌──(root@kali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 cmdline
Volatility Foundation Volatility Framework 2.6
************************************************************************
System pid: 4
************************************************************************
smss.exe pid: 540
Command line : \SystemRoot\System32\smss.exe
************************************************************************
csrss.exe pid: 596
Command line : C:\WINDOWS\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,3072,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ProfileControl=Off MaxRequestThreads=16
************************************************************************
winlogon.exe pid: 616
Command line : winlogon.exe
************************************************************************
services.exe pid: 672
Command line : C:\WINDOWS\system32\services.exe
************************************************************************
lsass.exe pid: 684
Command line : C:\WINDOWS\system32\lsass.exe
************************************************************************
vmacthlp.exe pid: 880
Command line : "C:\Program Files\VMware\VMware Tools\vmacthlp.exe"
************************************************************************
svchost.exe pid: 912
Command line : C:\WINDOWS\system32\svchost -k DcomLaunch
************************************************************************
svchost.exe pid: 980
Command line : C:\WINDOWS\system32\svchost -k rpcss
************************************************************************
svchost.exe pid: 1112
Command line : C:\WINDOWS\system32\svchost.exe -k netsvcs
************************************************************************
svchost.exe pid: 1144
Command line : C:\WINDOWS\system32\svchost.exe -k NetworkService
************************************************************************
VGAuthService.e pid: 1364
Command line : "C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe"
************************************************************************
explorer.exe pid: 1560
Command line : C:\WINDOWS\Explorer.EXE
************************************************************************
vmtoolsd.exe pid: 1640
Command line : "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"
************************************************************************
vmtoolsd.exe pid: 1724
Command line : "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr
************************************************************************
CTFMON.EXE pid: 1768
Command line : "C:\WINDOWS\system32\ctfmon.exe"
************************************************************************
wmiprvse.exe pid: 1900
Command line : C:\WINDOWS\system32\wbem\wmiprvse.exe
************************************************************************
svchost.exe pid: 1972
Command line : C:\WINDOWS\system32\svchost.exe -k LocalService
************************************************************************
WinRAR.exe pid: 296
Command line : "C:\Program Files\WinRAR\WinRAR.exe" "C:\Documents and Settings\Administrator\桌面\NTE2OQ==.zip"
************************************************************************
notepad.exe pid: 564
Command line : "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Documents and Settings\Administrator\桌面\wow.txt
************************************************************************
cmd.exe pid: 1628
Command line : "C:\WINDOWS\system32\cmd.exe"
************************************************************************
conime.exe pid: 1740
Command line : C:\WINDOWS\system32\conime.exe
************************************************************************
notepad.exe pid: 688
Command line : "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Documents and Settings\Administrator\桌面\wow.txt
************************************************************************
DumpIt.exe pid: 1576
Command line : "C:\Documents and Settings\Administrator\桌面\DumpIt.exe"发现两个可疑文件,一个是wow.txt,一个是NTE2OQ==.zip,分别dump下来
┌──(root@kali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 filescan | grep "NTE2OQ==.zip"
Volatility Foundation Volatility Framework 2.6
0x000000000222b028 1 0 RW-rw- \Device\HarddiskVolume1\Documents and Settings\Administrator\Recent\NTE2OQ==.zip.lnk
0x00000000022c2408 1 0 R--r-- \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\NTE2OQ==.zip
┌──(root@kali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 dumpfiles -Q 0x00000000022c2408 -D ./
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x022c2408 None \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\NTE2OQ==.zipdump下来的zip文件是file.None.0x81f82e38.dat,改名为NTE2OQ==.zip,顺带base64解密NTE2OQ==为5169,正好为解压缩密码,文件夹里是一个名为弗拉格.txt的文件,内容为key5:c00l},有效数据+1。
再dump文件wow.txt
┌──(root@kali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 filescan | grep "wow.txt"
Volatility Foundation Volatility Framework 2.6
0x0000000002255c70 1 0 -W-rwd \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\wow.txtrator\VMwareDnD\1c8d3301\wow.txt
0x00000000022c6b40 1 0 RW-rw- \Device\HarddiskVolume1\Documents and Settings\Administrator\Recent\wow.txt.lnk
┌──(root@kali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 dumpfiles -Q 0x0000000002255c70 -D ./
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x02255c70 None \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\wow.txtrator\VMwareDnD\1c8d3301\wow.txt将file.None.0x82016d48.dat改为wow.txt,打开得到key2:St3g0_,重复数据,问题不大,继续看回进程,发现无头绪,那就看看文件,常见可能会有隐藏信息的文件就是图片,所以先看看图片类的文件有没有蹊跷
──(root@kali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 filescan | grep "jpg\|jpeg\|png\|tif\|gif\|bmp" 1 ⨯
Volatility Foundation Volatility Framework 2.6
0x00000000022352c8 1 0 R--rwd \Device\HarddiskVolume1\secret.png
0x000000000237ef90 1 0 R--rwd \Device\HarddiskVolume1\WINDOWS\system32\wlnotify.dll
0x00000000023a1c28 1 0 RW-rw- \Device\HarddiskVolume1\Documents and Settings\Administrator\Recent\secret.png.lnk
0x0000000002416930 1 0 R--rwd \Device\HarddiskVolume1\WINDOWS\system32\wlnotify.dll上来就看到一个secret.png,dump下来
┌──(root@kali)-[~]
└─# volatility -f memory.raw --profile=WinXPSP2x86 dumpfiles -Q 0x00000000022352c8 -D ./
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x022352c8 None \Device\HarddiskVolume1\secret.png得到一张无法正常加载的图片,那必定是有点问题了,先binwalk分析一波,无异常。然后pngcheck检查,显示CRC校验码错误,那说明是高度隐写了,winhex打开修改高度(010 Editor也可)得到下图
E:\Misc\pngcheck-2.3.0-win32>pngcheck secret.png
secret.png CRC error in chunk IHDR (computed dafe1dad, expected d1dc106c)
ERROR: secret.png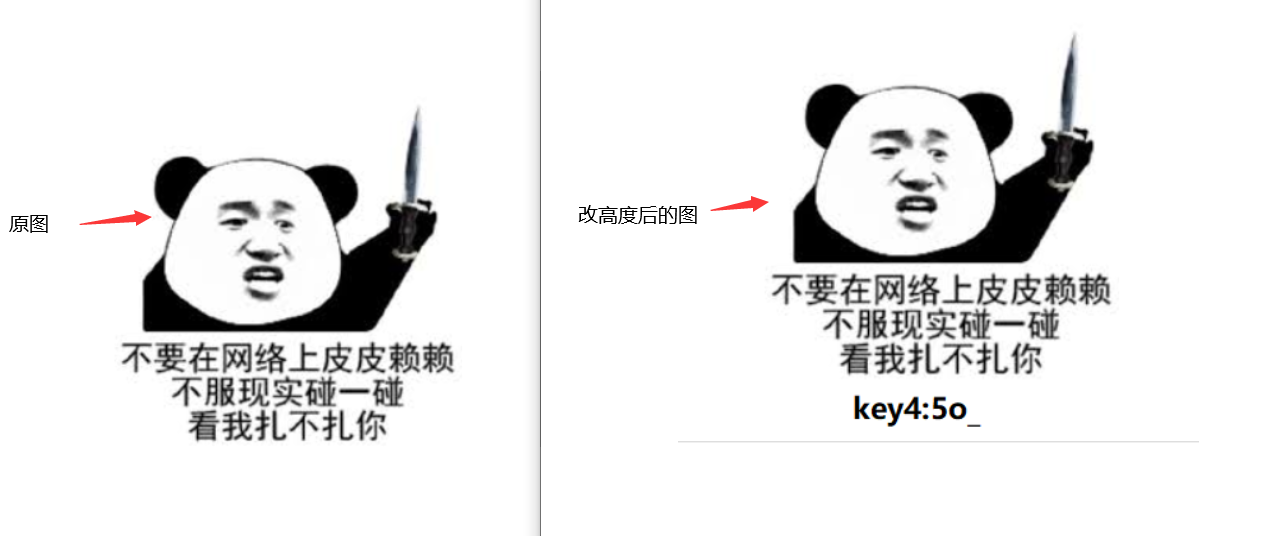
得到key4:5o_,那么现在flag已经齐全了为flag{7h3_St3g0_1s_5o_c00l}
这个题目到此为止了,通过这个简单套娃题,学到最基础的内存取证相关的思路。
Memory-2
老套路,分析镜像,查看进程
┌──(root@kali)-[~]
└─# volatility -f memory_file imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/root/桌面/memory_file)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80003dff0a0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80003e00d00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2020-08-27 16:45:05 UTC+0000
Image local date and time : 2020-08-28 00:45:05 +0800
┌──(root@kali)-[~]
└─# volatility -f memory_file --profile=Win7SP1x64 pslist
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
-------------------------------------------------------------------------------------------------------------------
0xfffffa80057db840 System 4 0 88 350 ------ 0 2020-08-27 16:42:15 UTC+0000
0xfffffa8006627b30 smss.exe 252 4 2 29 ------ 0 2020-08-27 16:42:15 UTC+0000
0xfffffa80060af890 csrss.exe 332 324 9 518 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8006ef1060 wininit.exe 372 324 3 77 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8006f178c0 csrss.exe 384 364 9 215 1 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8006f31060 winlogon.exe 420 364 6 121 1 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8006f65b30 services.exe 480 372 9 219 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8006f7ab30 lsass.exe 492 372 7 567 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8006f79b30 lsm.exe 500 372 10 146 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8006fd6b30 svchost.exe 608 480 10 354 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8007003b30 svchost.exe 676 480 7 283 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8007025430 svchost.exe 720 480 21 428 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8007061640 svchost.exe 820 480 20 407 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa8007089980 svchost.exe 868 480 45 1044 0 0 2020-08-27 16:42:16 UTC+0000
0xfffffa80070d4290 svchost.exe 988 480 13 488 0 0 2020-08-27 16:42:17 UTC+0000
0xfffffa8007110b30 svchost.exe 468 480 16 439 0 0 2020-08-27 16:42:17 UTC+0000
0xfffffa8007145b30 spoolsv.exe 544 480 15 278 0 0 2020-08-27 16:42:17 UTC+0000
0xfffffa80071666b0 svchost.exe 1052 480 19 319 0 0 2020-08-27 16:42:17 UTC+0000
0xfffffa8007229b30 VGAuthService. 1228 480 5 93 0 0 2020-08-27 16:42:17 UTC+0000
0xfffffa800727eb30 vmtoolsd.exe 1260 480 11 271 0 0 2020-08-27 16:42:18 UTC+0000
0xfffffa80066b4b30 dllhost.exe 1512 480 19 187 0 0 2020-08-27 16:42:18 UTC+0000
0xfffffa8007329630 WmiPrvSE.exe 1536 608 11 205 0 0 2020-08-27 16:42:18 UTC+0000
0xfffffa8007344b30 dllhost.exe 1620 480 18 202 0 0 2020-08-27 16:42:18 UTC+0000
0xfffffa8006506a20 msdtc.exe 1716 480 15 155 0 0 2020-08-27 16:42:19 UTC+0000
0xfffffa8006515510 taskhost.exe 1852 480 10 176 1 0 2020-08-27 16:42:19 UTC+0000
0xfffffa8006f61060 dwm.exe 1920 820 4 71 1 0 2020-08-27 16:42:20 UTC+0000
0xfffffa8006f2b620 explorer.exe 1940 1912 34 863 1 0 2020-08-27 16:42:20 UTC+0000
0xfffffa80073c48e0 vm3dservice.ex 1320 1940 3 40 1 0 2020-08-27 16:42:20 UTC+0000
0xfffffa80073c6b30 vmtoolsd.exe 1412 1940 9 178 1 0 2020-08-27 16:42:20 UTC+0000
0xfffffa80073fcb30 VSSVC.exe 1072 480 6 114 0 0 2020-08-27 16:42:20 UTC+0000
0xfffffa800703fb30 SearchIndexer. 2140 480 14 565 0 0 2020-08-27 16:42:26 UTC+0000
0xfffffa8007642b30 SearchProtocol 2208 2140 6 274 0 0 2020-08-27 16:42:26 UTC+0000
0xfffffa80076a2b30 SearchFilterHo 2232 2140 4 76 0 0 2020-08-27 16:42:27 UTC+0000
0xfffffa800656bb30 cmd.exe 2524 1940 1 22 1 0 2020-08-27 16:42:32 UTC+0000
0xfffffa800760a630 conhost.exe 2532 384 3 64 1 0 2020-08-27 16:42:32 UTC+0000
0xfffffa800760a060 WmiPrvSE.exe 2660 608 13 306 0 0 2020-08-27 16:42:38 UTC+0000
0xfffffa800662e1e0 svchost.exe 2556 480 12 143 0 0 2020-08-27 16:44:18 UTC+0000
0xfffffa80070d77b0 mscorsvw.exe 2440 480 8 106 0 1 2020-08-27 16:44:18 UTC+0000
0xfffffa8006571b30 mscorsvw.exe 2492 480 8 100 0 0 2020-08-27 16:44:18 UTC+0000
0xfffffa80076b1280 sppsvc.exe 2920 480 6 158 0 0 2020-08-27 16:44:19 UTC+0000
0xfffffa80060f8b30 svchost.exe 2836 480 12 331 0 0 2020-08-27 16:44:19 UTC+0000
0xfffffa8005830060 WmiApSrv.exe 1168 480 6 110 0 0 2020-08-27 16:44:46 UTC+0000
0xfffffa80062acb30 dllhost.exe 2824 608 6 84 0 0 2020-08-27 16:44:59 UTC+0000
0xfffffa8006274420 dllhost.exe 2820 608 6 87 1 0 2020-08-27 16:45:04 UTC+0000
0xfffffa8005860060 DumpIt.exe 2260 1940 2 45 1 1 2020-08-27 16:45:04 UTC+0000
0xfffffa80061e8b30 conhost.exe 692 384 2 63 1 0 2020-08-27 16:45:04 UTC+0000可疑进程不多,还是先看看cmd吧
┌──(root@kali)-[~]
└─# volatility -f memory_file --profile=Win7SP1x64 cmdscan
Volatility Foundation Volatility Framework 2.6
**************************************************
CommandProcess: conhost.exe Pid: 2532
CommandHistory: 0x3690e0 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 12 LastAdded: 11 LastDisplayed: 11
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 @ 0x3415f0: whoami
Cmd #1 @ 0x341630: ipconfig
Cmd #2 @ 0x341650: chdir
Cmd #3 @ 0x355890: mkdir c1scn_a0d_fi1e
Cmd #4 @ 0x341670: cd c:\
Cmd #5 @ 0x358490: dir
Cmd #6 @ 0x3584a0: pwd
Cmd #7 @ 0x341690: path
Cmd #8 @ 0x3584b0: dir
Cmd #9 @ 0x3584c0: env
Cmd #10 @ 0x3416b0: system
Cmd #11 @ 0x3416d0: quit
**************************************************
CommandProcess: conhost.exe Pid: 692
CommandHistory: 0x3a90e0 Application: DumpIt.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60发现文件夹c1scn_a0d_fi1e,看看文件夹下有啥
┌──(root@kali)-[~]
└─# volatility -f memory_file --profile=Win7SP1x64 filescan | grep "c1scn_a0d_fi1e"
Volatility Foundation Volatility Framework 2.6
0x00000000177a14f0 2 1 R--rwd \Device\HarddiskVolume1\Program Files\Common Files\c1scn_a0d_fi1e
0x00000000181283c0 2 1 R--rwd \Device\HarddiskVolume1\Program Files\Common Files\c1scn_a0d_fi1e
0x00000000185caf20 16 0 R--rwd \Device\HarddiskVolume1\Program Files\Common Files\c1scn_a0d_fi1e\F14gggggg发现明显的F14gggggg文件,volatility无法直接dump文件,兜兜转转一大圈才得知需要取证大师才能dump该文件。

文件dump下来后记事本打开发现乱码,然后winhex打开,发现有蹊跷!
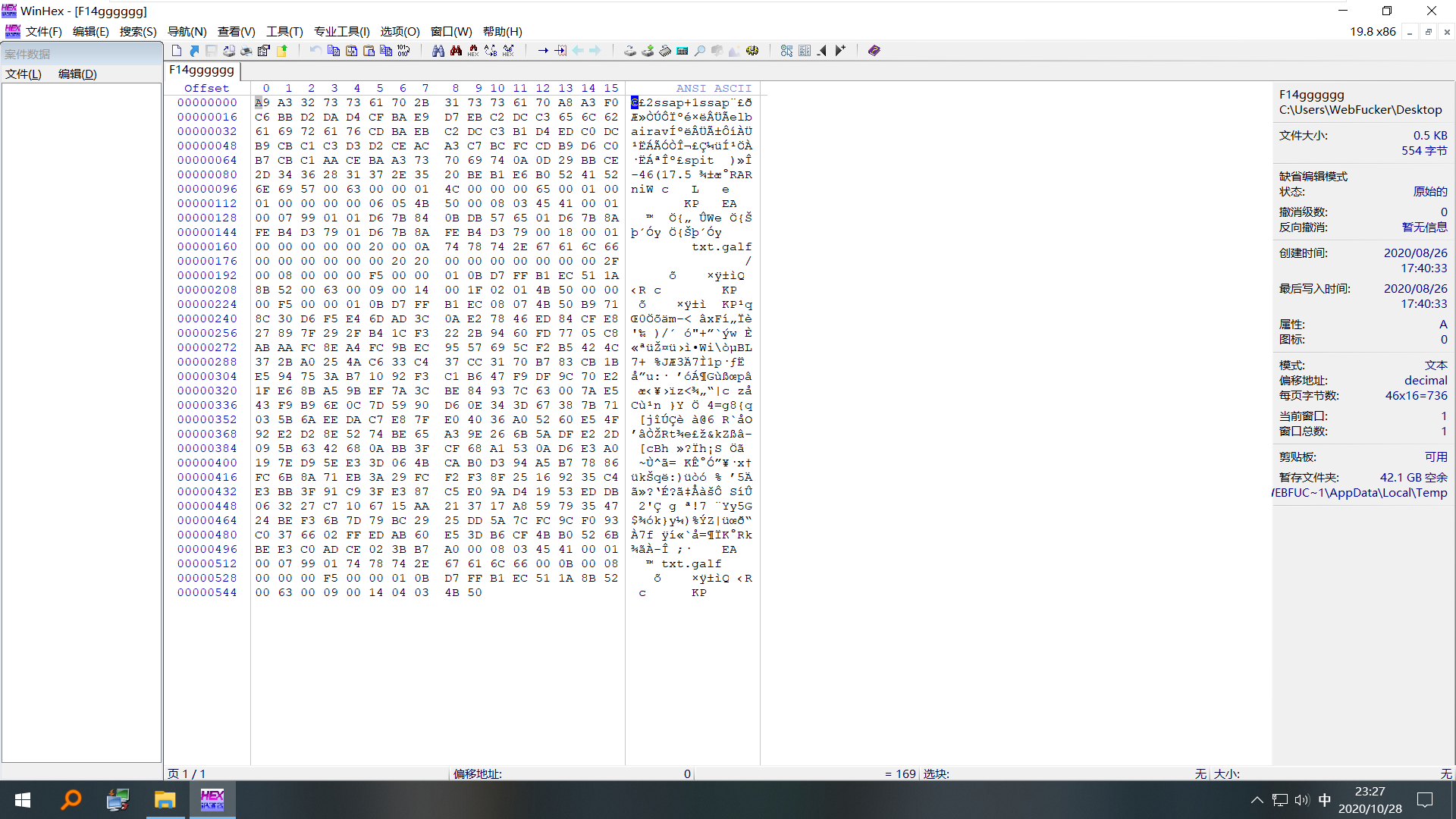
zip压缩的老考点了,16进制代码倒叙,直接脚本跑出正确的zip,
#!/usr/bin/env python-3.8
# -*- coding: utf-8 -*-
# @Project: Hello Python!
# @File : 9.2-zip十六进制反序输出
# @Author : Tr0jAn <webfker@oulook.com>
# @Date : 2020-09-17
from __future__ import print_function
import binascii
f = open('F14gggggg', 'rb')
n = 0
s = f.read(1)
List = []
while s:
byte = ord(s)
n = n + 1
List.append('%02x' % byte)
s = f.read(1)
f.close()
result = open("result.zip", "ab")
final = ''
for i in range(len(List) - 1, 0, -1):
final = final + List[i]
data = binascii.a2b_hex(final.encode())
result.write(data)
result.close()得到result.zip,但是有密码,winhex看是不是伪加密,发现并不是,但是末尾有提示
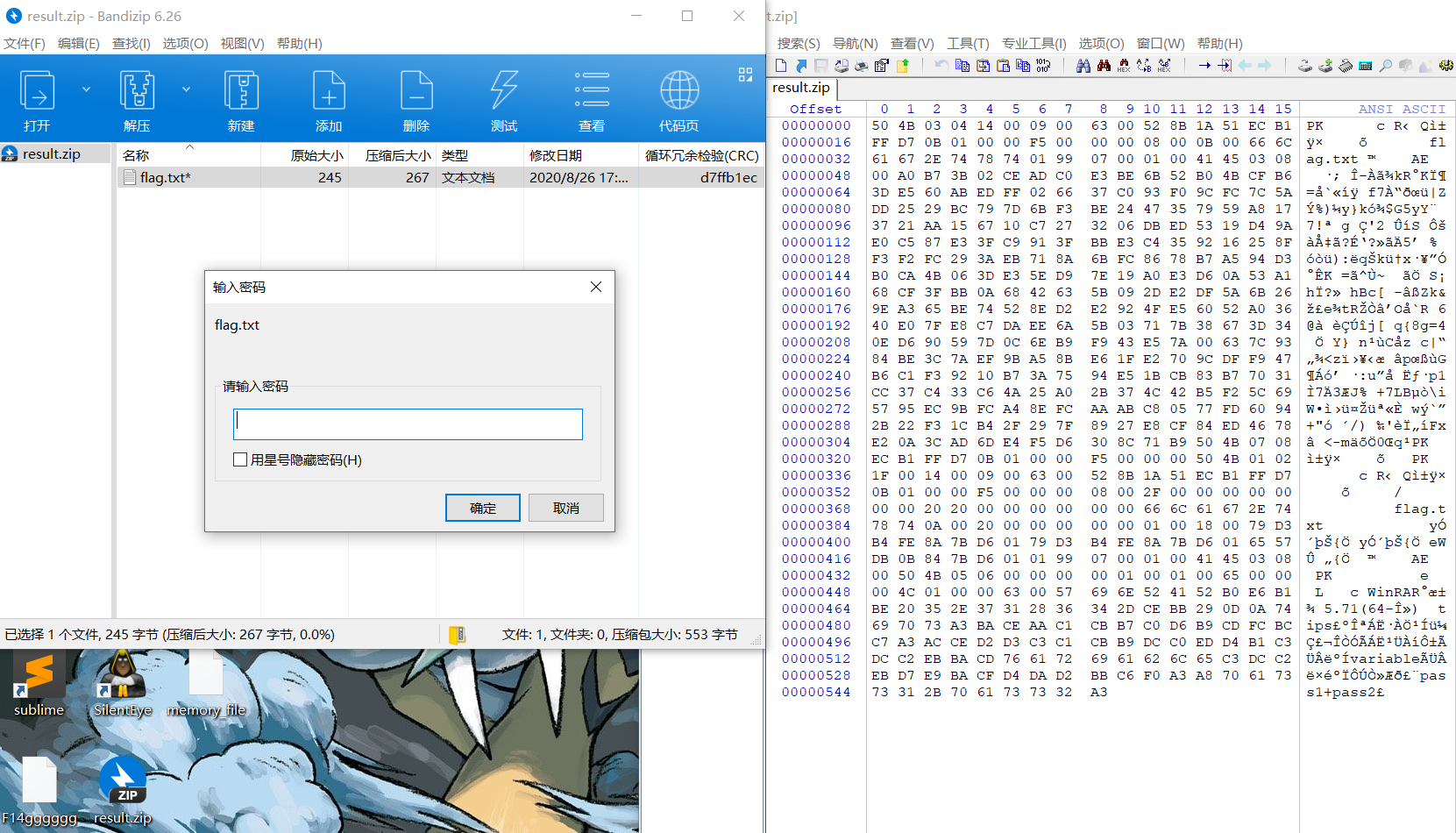
得到提示:(也可以kali下strings查看)
tips
variable
pass1+pass2
┌──(root@kali)-[~]
└─# strings result.zip
flag.txt
$G5yY
hBc[ -
q{8g=4
+7LB
flag.txt
WinRAR
5.71(64-
tips
variable
pass1+pass2变量,密码两段。那很容易联想到是系统变量,系统密码啥的
┌──(root@kali)-[~]
└─# volatility -f memory_file --profile=Win7SP1x64 envars | grep "Password"
Volatility Foundation Volatility Framework 2.6
332 csrss.exe 0x0000000000411320 Password .e#9V4pxW!N
384 csrss.exe 0x00000000003f1320 Password .e#9V4pxW!N
420 winlogon.exe 0x000000000031e630 Password .e#9V4pxW!N
480 services.exe 0x0000000000141320 Password .e#9V4pxW!N
492 lsass.exe 0x0000000000241320 Password .e#9V4pxW!N
500 lsm.exe 0x0000000000161320 Password .e#9V4pxW!N
608 svchost.exe 0x0000000000241320 Password .e#9V4pxW!N
676 svchost.exe 0x0000000000101320 Password .e#9V4pxW!N
720 svchost.exe 0x0000000000171320 Password .e#9V4pxW!N
820 svchost.exe 0x0000000000121320 Password .e#9V4pxW!N
868 svchost.exe 0x0000000000331320 Password .e#9V4pxW!N
988 svchost.exe 0x0000000000171320 Password .e#9V4pxW!N
468 svchost.exe 0x00000000002b1320 Password .e#9V4pxW!N
544 spoolsv.exe 0x0000000000141320 Password .e#9V4pxW!N
1052 svchost.exe 0x0000000000091320 Password .e#9V4pxW!N
1228 VGAuthService. 0x0000000000431320 Password .e#9V4pxW!N
1260 vmtoolsd.exe 0x00000000001f1320 Password .e#9V4pxW!N
1512 dllhost.exe 0x0000000000181320 Password .e#9V4pxW!N
1536 WmiPrvSE.exe 0x00000000003e1320 Password .e#9V4pxW!N
1620 dllhost.exe 0x00000000002d1320 Password .e#9V4pxW!N
1716 msdtc.exe 0x0000000000351320 Password .e#9V4pxW!N
1852 taskhost.exe 0x0000000000051320 Password .e#9V4pxW!N
1920 dwm.exe 0x0000000000401320 Password .e#9V4pxW!N
1940 explorer.exe 0x00000000034b9860 Password .e#9V4pxW!N
1320 vm3dservice.ex 0x0000000000311320 Password .e#9V4pxW!N
1412 vmtoolsd.exe 0x00000000003a1320 Password .e#9V4pxW!N
1072 VSSVC.exe 0x0000000000401320 Password .e#9V4pxW!N
2140 SearchIndexer. 0x000000000048c920 Password .e#9V4pxW!N
2208 SearchProtocol 0x0000000000251320 Password .e#9V4pxW!N
2232 SearchFilterHo 0x0000000000341320 Password .e#9V4pxW!N
2524 cmd.exe 0x000000000035bf40 Password .e#9V4pxW!N
2532 conhost.exe 0x0000000000340980 Password .e#9V4pxW!N
2660 WmiPrvSE.exe 0x00000000003d1320 Password .e#9V4pxW!N
2556 svchost.exe 0x0000000000211320 Password .e#9V4pxW!N
2556 svchost.exe 0x0000000000211320 Path C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;Password .e#9V4pxW!N
2440 mscorsvw.exe 0x00000000001c1320 Password .e#9V4pxW!N
2440 mscorsvw.exe 0x00000000001c1320 Path C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;Password .e#9V4pxW!N
2492 mscorsvw.exe 0x0000000000301320 Password .e#9V4pxW!N
2492 mscorsvw.exe 0x0000000000301320 Path C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;Password .e#9V4pxW!N
2920 sppsvc.exe 0x00000000002d1320 Password .e#9V4pxW!N
2920 sppsvc.exe 0x00000000002d1320 Path C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;Password .e#9V4pxW!N
2836 svchost.exe 0x00000000001abf90 Password .e#9V4pxW!N
2836 svchost.exe 0x00000000001abf90 Path C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;Password .e#9V4pxW!N
1168 WmiApSrv.exe 0x0000000000081320 Password .e#9V4pxW!N
1168 WmiApSrv.exe 0x0000000000081320 Path C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;Password .e#9V4pxW!N
2824 dllhost.exe 0x00000000002b1320 Password .e#9V4pxW!N
2820 dllhost.exe 0x00000000002a1320 Password .e#9V4pxW!N
2260 DumpIt.exe 0x0000000000341320 Password .e#9V4pxW!N
2260 DumpIt.exe 0x0000000000341320 Path C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;Password .e#9V4pxW!N
692 conhost.exe 0x0000000000380980 Password .e#9V4pxW!N环境变量中的Password全部都是.e#9V4pxW!N,基本确定是一个pass了,再看看系统密码
┌──(root@kali)-[~]
└─# volatility -f memory_file --profile=Win7SP1x64 hashdump
Volatility Foundation Volatility Framework 2.6
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
ciscn:1000:aad3b435b51404eeaad3b435b51404ee:570a9a65db8fba761c1008a51d4c95ab:::
最后只有ciscn的密码能查到内容为Admin@123,用的在线网址
那压缩包密码就是他俩排列组合了,发现是Admin@123.e#9V4pxW!N,解压出flag.txt,得到如下内容
#想啥呢,怎么会那么轻易就还给你,我留下了reg痕迹(你可知道远程端口怎么修改),如果你能找到,那么这场游戏,也就结束了...
U2FsdGVkX1+lG4QYPzfyv1BZ4BclqoRqcrNu7KIDFeL9aTD/qKl/IA2zh2hdGo6YKOW7tXhb百度查reg远程端口修改,查到在注册表中修改两处
第一处: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\Wds\rdpwd\Tds\tcp
第二处: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp对应题目中的win版本,两处位置在
第一处: HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Terminal Server\Wds\rdpwd\Tds\tcp
第二处: HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Terminal Server\WinStations\RDP-Tcp然后分别查询两处位置的信息
┌──(root@kali)-[~]
└─# volatility -f memory_file --profile=Win7SP1x64 -o 0xfffff8a000021260 printkey -K 'ControlSet001\Control\Terminal Server\Wds\rdpwd\Tds\tcp'
Volatility Foundation Volatility Framework 2.6
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \REGISTRY\MACHINE\SYSTEM
Key name: tcp (S)
Last updated: 2020-08-27 16:42:43 UTC+0000
Subkeys:
Values:
REG_DWORD InteractiveDelay : (S) 10
REG_DWORD OutBufCount : (S) 6
REG_DWORD OutBufDelay : (S) 100
REG_DWORD OutBufLength : (S) 530
REG_DWORD PdClass : (S) 2
REG_SZ PdDLL : (S) tdtcp
REG_DWORD PdFlag : (S) 78
REG_SZ PdName : (S) tcp
REG_DWORD PortNumber : (S) 3389
REG_MULTI_SZ RequiredPds : (S) ['tssecsrv', '', '']
REG_SZ ServiceName : (S) tcpip
REG_SZ RC4_key1 : (S) We1c0me_┌──(root@kali)-[~]
└─# volatility -f memory_file --profile=Win7SP1x64 -o 0xfffff8a000021260 printkey -K 'ControlSet001\Control\Terminal Server\WinStations\RDP-Tcp'
Volatility Foundation Volatility Framework 2.6
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \REGISTRY\MACHINE\SYSTEM
Key name: RDP-Tcp (S)
Last updated: 2020-08-27 16:42:43 UTC+0000
Subkeys:
(S) TSMMRemotingAllowedApps
Values:
REG_SZ AudioEnumeratorDll : (S) rdpendp.dll
REG_DWORD Callback : (S) 0
REG_SZ CallbackNumber : (S)
REG_DWORD CdClass : (S) 0
REG_SZ CdDLL : (S)
REG_DWORD CdFlag : (S) 0
REG_SZ CdName : (S)
REG_SZ CfgDll : (S) RDPCFGEX.DLL
REG_DWORD ColorDepth : (S) 5
REG_SZ Comment : (S)
REG_SZ Domain : (S)
REG_DWORD DrawGdiplusSupportLevel : (S) 1
REG_DWORD fAllowSecProtocolNegotiation : (S) 1
REG_DWORD fAutoClientDrives : (S) 1
REG_DWORD fAutoClientLpts : (S) 1
REG_DWORD fDisableAudioCapture : (S) 1
REG_DWORD fDisableCam : (S) 0
REG_DWORD fDisableCcm : (S) 0
REG_DWORD fDisableCdm : (S) 0
REG_DWORD fDisableClip : (S) 0
REG_DWORD fDisableCpm : (S) 0
REG_DWORD fDisableEncryption : (S) 1
REG_DWORD fDisableExe : (S) 0
REG_DWORD fDisableLPT : (S) 0
REG_DWORD fEnableWinStation : (S) 1
REG_DWORD fForceClientLptDef : (S) 1
REG_DWORD fHomeDirectoryMapRoot : (S) 0
REG_DWORD fInheritAutoClient : (S) 1
REG_DWORD fInheritAutoLogon : (S) 1
REG_DWORD fInheritCallback : (S) 0
REG_DWORD fInheritCallbackNumber : (S) 1
REG_DWORD fInheritColorDepth : (S) 0
REG_DWORD fInheritInitialProgram : (S) 1
REG_DWORD fInheritMaxDisconnectionTime : (S) 1
REG_DWORD fInheritMaxIdleTime : (S) 1
REG_DWORD fInheritMaxSessionTime : (S) 1
REG_DWORD fInheritReconnectSame : (S) 1
REG_DWORD fInheritResetBroken : (S) 1
REG_DWORD fInheritSecurity : (S) 0
REG_DWORD fInheritShadow : (S) 1
REG_DWORD fLogonDisabled : (S) 0
REG_DWORD fPromptForPassword : (S) 0
REG_DWORD fReconnectSame : (S) 0
REG_DWORD fResetBroken : (S) 0
REG_DWORD fUseDefaultGina : (S) 0
REG_SZ InitialProgram : (S)
REG_DWORD InputBufferLength : (S) 2048
REG_DWORD InteractiveDelay : (S) 50
REG_DWORD KeepAliveTimeout : (S) 0
REG_DWORD KeyboardLayout : (S) 0
REG_DWORD LanAdapter : (S) 0
REG_SZ LoadableProtocol_Object : (S) {18b726bb-6fe6-4fb9-9276-ed57ce7c7cb2}
REG_DWORD MaxConnectionTime : (S) 0
REG_DWORD MaxDisconnectionTime : (S) 0
REG_DWORD MaxIdleTime : (S) 0
REG_DWORD MaxInstanceCount : (S) 4294967295
REG_DWORD MinEncryptionLevel : (S) 2
REG_SZ NWLogonServer : (S)
REG_DWORD OutBufCount : (S) 6
REG_DWORD OutBufDelay : (S) 100
REG_DWORD OutBufLength : (S) 530
REG_SZ Password : (S)
REG_DWORD PdClass : (S) 2
REG_DWORD PdClass1 : (S) 11
REG_SZ PdDLL : (S) tdtcp
REG_SZ PdDLL1 : (S) tssecsrv
REG_DWORD PdFlag : (S) 78
REG_DWORD PdFlag1 : (S) 0
REG_SZ PdName : (S) tcp
REG_SZ PdName1 : (S) tssecsrv
REG_DWORD PortNumber : (S) 3389
REG_DWORD SecurityLayer : (S) 1
REG_DWORD Shadow : (S) 1
REG_DWORD UserAuthentication : (S) 0
REG_SZ Username : (S)
REG_SZ WdDLL : (S) rdpwd
REG_DWORD WdFlag : (S) 54
REG_SZ WdName : (S) Microsoft RDP 7.1
REG_SZ WdPrefix : (S) RDP
REG_SZ WFProfilePath : (S)
REG_SZ WorkDirectory : (S)
REG_SZ WsxDLL : (S) rdpwsx
REG_SZ RC4_key2 : (S) c1scn@得到两段RC4密钥,拼起来得到We1c0me_c1scn@,联想到刚才的字符串,直接在线网站一波解密解密得到flag
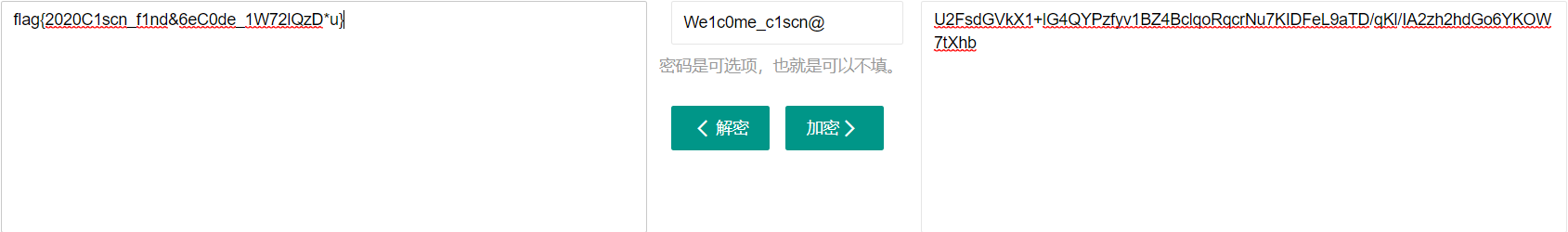
flag{2020C1scn_f1nd&6eC0de_1W72lQzD*u}



师傅,如果只是单纯的逆序十六进制数据,可以用切片
with open('1.zip', 'rb') as f:
bin_data = f.read()
with open('1.new.zip', 'wb') as f:
f.write(bin_data[::-1])
可以可以,给大佬递茶d=====( ̄▽ ̄*)b