Mal
Description
popped up message destroyed me.
Flag Format: Securinets{flag}Solution
General Forensic Challenges
root@kali:~# vol -f mal.raw imageinfo
Volatility Foundation Volatility Framework 2.6.1
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/root/Securinets CTF Quals 2022/mal.raw)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf800029fe0a0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff800029ffd00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2022-04-09 12:28:27 UTC+0000
Image local date and time : 2022-04-09 05:28:27 -0700
root@kali:~# vol -f mal.raw --profile=Win7SP1x64 pslist
Volatility Foundation Volatility Framework 2.6.1
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0xfffffa8018dc1040 System 4 0 78 550 ------ 0 2022-04-09 10:40:44 UTC+0000
0xfffffa80197bd8f0 smss.exe 236 4 2 29 ------ 0 2022-04-09 10:40:44 UTC+0000
0xfffffa801a1deb30 csrss.exe 312 304 8 377 0 0 2022-04-09 10:40:50 UTC+0000
0xfffffa801a1f3b30 csrss.exe 360 352 9 676 1 0 2022-04-09 10:40:51 UTC+0000
0xfffffa801a1fa8c0 wininit.exe 368 304 3 74 0 0 2022-04-09 10:40:51 UTC+0000
0xfffffa801a206b30 winlogon.exe 396 352 4 113 1 0 2022-04-09 10:40:51 UTC+0000
0xfffffa801a270b30 services.exe 456 368 6 200 0 0 2022-04-09 10:40:53 UTC+0000
0xfffffa801a284b30 lsass.exe 464 368 7 605 0 0 2022-04-09 10:40:54 UTC+0000
0xfffffa801a28ab30 lsm.exe 472 368 10 147 0 0 2022-04-09 10:40:54 UTC+0000
0xfffffa801a359b30 svchost.exe 560 456 10 366 0 0 2022-04-09 10:40:57 UTC+0000
0xfffffa801a20d060 svchost.exe 636 456 8 271 0 0 2022-04-09 10:40:58 UTC+0000
0xfffffa801a2b3150 svchost.exe 716 456 21 475 0 0 2022-04-09 10:40:58 UTC+0000
0xfffffa801a2e4060 svchost.exe 768 456 17 381 0 0 2022-04-09 10:40:59 UTC+0000
0xfffffa801a30b060 svchost.exe 796 456 29 909 0 0 2022-04-09 10:40:59 UTC+0000
0xfffffa801a368060 svchost.exe 964 456 13 314 0 0 2022-04-09 10:41:02 UTC+0000
0xfffffa801a331060 svchost.exe 260 456 14 470 0 0 2022-04-09 10:41:04 UTC+0000
0xfffffa801a446850 spoolsv.exe 1052 456 12 263 0 0 2022-04-09 10:41:09 UTC+0000
0xfffffa801a45c960 svchost.exe 1080 456 18 311 0 0 2022-04-09 10:41:09 UTC+0000
0xfffffa801a4b94a0 svchost.exe 1192 456 11 192 0 0 2022-04-09 10:41:11 UTC+0000
0xfffffa801a407b30 svchost.exe 1580 456 6 91 0 0 2022-04-09 10:41:20 UTC+0000
0xfffffa801a61eb30 taskhost.exe 1780 456 9 211 1 0 2022-04-09 10:41:22 UTC+0000
0xfffffa801a5b9500 dwm.exe 1896 768 3 70 1 0 2022-04-09 10:41:22 UTC+0000
0xfffffa801a525060 explorer.exe 1904 1872 34 1080 1 0 2022-04-09 10:41:22 UTC+0000
0xfffffa801a700b30 SearchIndexer. 588 456 14 704 0 0 2022-04-09 10:41:35 UTC+0000
0xfffffa801a0b16e0 sppsvc.exe 1876 456 4 144 0 0 2022-04-09 10:43:26 UTC+0000
0xfffffa801a3deb30 svchost.exe 1392 456 13 320 0 0 2022-04-09 10:43:29 UTC+0000
0xfffffa801a986060 firefox.exe 2808 892 79 1521 1 1 2022-04-09 11:31:11 UTC+0000
0xfffffa801a840b30 firefox.exe 2708 2808 34 372 1 1 2022-04-09 11:31:14 UTC+0000
0xfffffa801a7ac060 firefox.exe 1776 2808 18 281 1 1 2022-04-09 11:31:14 UTC+0000
0xfffffa801a0acb30 firefox.exe 2320 2808 18 286 1 1 2022-04-09 11:31:20 UTC+0000
0xfffffa801aa13b30 firefox.exe 2544 2808 18 285 1 1 2022-04-09 11:31:30 UTC+0000
0xfffffa801a546b30 firefox.exe 2024 2808 19 295 1 1 2022-04-09 11:31:50 UTC+0000
0xfffffa801aa0e6b0 taskhost.exe 2828 456 5 189 1 0 2022-04-09 11:36:15 UTC+0000
0xfffffa801abf38e0 taskmgr.exe 2464 1904 5 118 1 0 2022-04-09 11:51:09 UTC+0000
0xfffffa801a92d690 firefox.exe 2540 2808 20 290 1 1 2022-04-09 12:24:54 UTC+0000
0xfffffa801a889060 audiodg.exe 1376 716 8 147 0 0 2022-04-09 12:25:15 UTC+0000
0xfffffa801aa1bb30 firefox.exe 2204 2808 26 321 1 1 2022-04-09 12:26:04 UTC+0000
0xfffffa801a9a7b30 firefox.exe 3128 2808 20 292 1 1 2022-04-09 12:26:07 UTC+0000
0xfffffa801ac24b30 firefox.exe 3232 2808 20 290 1 1 2022-04-09 12:26:09 UTC+0000
0xfffffa801ac90b30 firefox.exe 3320 2808 20 290 1 1 2022-04-09 12:26:11 UTC+0000
0xfffffa801acb8060 StikyNot.exe 3888 1904 9 176 1 0 2022-04-09 12:26:22 UTC+0000
0xfffffa801ad8bb30 firefox.exe 4040 2808 20 290 1 1 2022-04-09 12:26:24 UTC+0000
0xfffffa801ad865b0 notepad.exe 1360 1904 1 60 1 0 2022-04-09 12:26:25 UTC+0000
0xfffffa801adadb30 firefox.exe 2384 2808 9 185 1 1 2022-04-09 12:26:26 UTC+0000
0xfffffa8019467170 firefox.exe 3220 2808 16 270 1 1 2022-04-09 12:26:29 UTC+0000
0xfffffa80193ef260 Solitaire.exe 2152 1904 9 226 1 0 2022-04-09 12:26:29 UTC+0000
0xfffffa801a88da70 svchost.exe 2492 456 5 77 0 0 2022-04-09 12:27:25 UTC+0000
0xfffffa801a970a90 firef0x.exeexe 3492 1904 8 198 1 1 2022-04-09 12:27:38 UTC+0000
0xfffffa801a3edb30 WindowsUpdater 3468 3492 1 74 1 1 2022-04-09 12:27:38 UTC+0000
0xfffffa801ad30560 WerFault.exe 3996 2492 6 133 1 1 2022-04-09 12:27:38 UTC+0000
0xfffffa801ad04060 firefox.exe 1032 2808 19 280 1 1 2022-04-09 12:27:44 UTC+0000
0xfffffa801a9ec6c0 firefox.exe 2860 2808 18 276 1 1 2022-04-09 12:28:17 UTC+0000
0xfffffa801acd5060 DumpIt.exe 3624 1904 2 45 1 1 2022-04-09 12:28:24 UTC+0000
0xfffffa801a95f3e0 conhost.exe 4036 360 2 53 1 0 2022-04-09 12:28:24 UTC+0000You can see that at the end there is a firef0x.exeexe suspicious process, dump out the program found to be an ordinary Trojan, not too much use value.
root@kali:~# vol -f mal.raw --profile=Win7SP1x64 pstree
Volatility Foundation Volatility Framework 2.6.1
Name Pid PPid Thds Hnds Time
-------------------------------------------------- ------ ------ ------ ------ ----
0xfffffa801a1deb30:csrss.exe 312 304 8 377 2022-04-09 10:40:50 UTC+0000
0xfffffa801a1fa8c0:wininit.exe 368 304 3 74 2022-04-09 10:40:51 UTC+0000
. 0xfffffa801a270b30:services.exe 456 368 6 200 2022-04-09 10:40:53 UTC+0000
.. 0xfffffa801a2e4060:svchost.exe 768 456 17 381 2022-04-09 10:40:59 UTC+0000
... 0xfffffa801a5b9500:dwm.exe 1896 768 3 70 2022-04-09 10:41:22 UTC+0000
.. 0xfffffa801a3deb30:svchost.exe 1392 456 13 320 2022-04-09 10:43:29 UTC+0000
.. 0xfffffa801a331060:svchost.exe 260 456 14 470 2022-04-09 10:41:04 UTC+0000
.. 0xfffffa801a30b060:svchost.exe 796 456 29 909 2022-04-09 10:40:59 UTC+0000
.. 0xfffffa801a4b94a0:svchost.exe 1192 456 11 192 2022-04-09 10:41:11 UTC+0000
.. 0xfffffa801a446850:spoolsv.exe 1052 456 12 263 2022-04-09 10:41:09 UTC+0000
.. 0xfffffa801a407b30:svchost.exe 1580 456 6 91 2022-04-09 10:41:20 UTC+0000
.. 0xfffffa801a359b30:svchost.exe 560 456 10 366 2022-04-09 10:40:57 UTC+0000
.. 0xfffffa801a45c960:svchost.exe 1080 456 18 311 2022-04-09 10:41:09 UTC+0000
.. 0xfffffa801a88da70:svchost.exe 2492 456 5 77 2022-04-09 12:27:25 UTC+0000
... 0xfffffa801ad30560:WerFault.exe 3996 2492 6 133 2022-04-09 12:27:38 UTC+0000
.. 0xfffffa801a368060:svchost.exe 964 456 13 314 2022-04-09 10:41:02 UTC+0000
.. 0xfffffa801aa0e6b0:taskhost.exe 2828 456 5 189 2022-04-09 11:36:15 UTC+0000
.. 0xfffffa801a700b30:SearchIndexer. 588 456 14 704 2022-04-09 10:41:35 UTC+0000
.. 0xfffffa801a2b3150:svchost.exe 716 456 21 475 2022-04-09 10:40:58 UTC+0000
... 0xfffffa801a889060:audiodg.exe 1376 716 8 147 2022-04-09 12:25:15 UTC+0000
.. 0xfffffa801a0b16e0:sppsvc.exe 1876 456 4 144 2022-04-09 10:43:26 UTC+0000
.. 0xfffffa801a61eb30:taskhost.exe 1780 456 9 211 2022-04-09 10:41:22 UTC+0000
.. 0xfffffa801a20d060:svchost.exe 636 456 8 271 2022-04-09 10:40:58 UTC+0000
. 0xfffffa801a284b30:lsass.exe 464 368 7 605 2022-04-09 10:40:54 UTC+0000
. 0xfffffa801a28ab30:lsm.exe 472 368 10 147 2022-04-09 10:40:54 UTC+0000
0xfffffa8018dc1040:System 4 0 78 550 2022-04-09 10:40:44 UTC+0000
. 0xfffffa80197bd8f0:smss.exe 236 4 2 29 2022-04-09 10:40:44 UTC+0000
0xfffffa801a986060:firefox.exe 2808 892 79 1521 2022-04-09 11:31:11 UTC+0000
. 0xfffffa801a9ec6c0:firefox.exe 2860 2808 18 276 2022-04-09 12:28:17 UTC+0000
. 0xfffffa801ad04060:firefox.exe 1032 2808 19 280 2022-04-09 12:27:44 UTC+0000
. 0xfffffa801a92d690:firefox.exe 2540 2808 20 290 2022-04-09 12:24:54 UTC+0000
. 0xfffffa801a0acb30:firefox.exe 2320 2808 18 286 2022-04-09 11:31:20 UTC+0000
. 0xfffffa801aa1bb30:firefox.exe 2204 2808 26 321 2022-04-09 12:26:04 UTC+0000
. 0xfffffa801a840b30:firefox.exe 2708 2808 34 372 2022-04-09 11:31:14 UTC+0000
. 0xfffffa801ad8bb30:firefox.exe 4040 2808 20 290 2022-04-09 12:26:24 UTC+0000
. 0xfffffa801ac24b30:firefox.exe 3232 2808 20 290 2022-04-09 12:26:09 UTC+0000
. 0xfffffa801a546b30:firefox.exe 2024 2808 19 295 2022-04-09 11:31:50 UTC+0000
. 0xfffffa801a7ac060:firefox.exe 1776 2808 18 281 2022-04-09 11:31:14 UTC+0000
. 0xfffffa801adadb30:firefox.exe 2384 2808 9 185 2022-04-09 12:26:26 UTC+0000
. 0xfffffa801aa13b30:firefox.exe 2544 2808 18 285 2022-04-09 11:31:30 UTC+0000
. 0xfffffa801a9a7b30:firefox.exe 3128 2808 20 292 2022-04-09 12:26:07 UTC+0000
. 0xfffffa8019467170:firefox.exe 3220 2808 16 270 2022-04-09 12:26:29 UTC+0000
. 0xfffffa801ac90b30:firefox.exe 3320 2808 20 290 2022-04-09 12:26:11 UTC+0000
0xfffffa801a206b30:winlogon.exe 396 352 4 113 2022-04-09 10:40:51 UTC+0000
0xfffffa801a1f3b30:csrss.exe 360 352 9 676 2022-04-09 10:40:51 UTC+0000
. 0xfffffa801a95f3e0:conhost.exe 4036 360 2 53 2022-04-09 12:28:24 UTC+0000
0xfffffa801a525060:explorer.exe 1904 1872 34 1080 2022-04-09 10:41:22 UTC+0000
. 0xfffffa801acb8060:StikyNot.exe 3888 1904 9 176 2022-04-09 12:26:22 UTC+0000
. 0xfffffa801abf38e0:taskmgr.exe 2464 1904 5 118 2022-04-09 11:51:09 UTC+0000
. 0xfffffa801a970a90:firef0x.exeexe 3492 1904 8 198 2022-04-09 12:27:38 UTC+0000
.. 0xfffffa801a3edb30:WindowsUpdater 3468 3492 1 74 2022-04-09 12:27:38 UTC+0000
. 0xfffffa801acd5060:DumpIt.exe 3624 1904 2 45 2022-04-09 12:28:24 UTC+0000
. 0xfffffa801ad865b0:notepad.exe 1360 1904 1 60 2022-04-09 12:26:25 UTC+0000
. 0xfffffa80193ef260:Solitaire.exe 2152 1904 9 226 2022-04-09 12:26:29 UTC+0000Check the process tree to find firef0x.exeexe has a child process WindowsUpdater, dump down the process found to be msf Trojan.
root@kali:~# vol -f mal.raw --profile=Win7SP1x64 filescan | grep WindowsUpdater
Volatility Foundation Volatility Framework 2.6.1
0x000000007df7b140 3 0 R--r-d \Device\HarddiskVolume2\Users\CTF\Videos\WindowsUpdater.exe
0x000000007e761b20 2 0 R--r-d \Device\HarddiskVolume2\Users\CTF\Downloads\WindowsUpdater.exe
root@kali:~# vol -f mal.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000007e761b20 -D .
Volatility Foundation Volatility Framework 2.6.1
ImageSectionObject 0x7e761b20 None \Device\HarddiskVolume2\Users\CTF\Downloads\WindowsUpdater.exe
DataSectionObject 0x7e761b20 None \Device\HarddiskVolume2\Users\CTF\Downloads\WindowsUpdater.exeCombine the description of the topic and run it to get the flag.
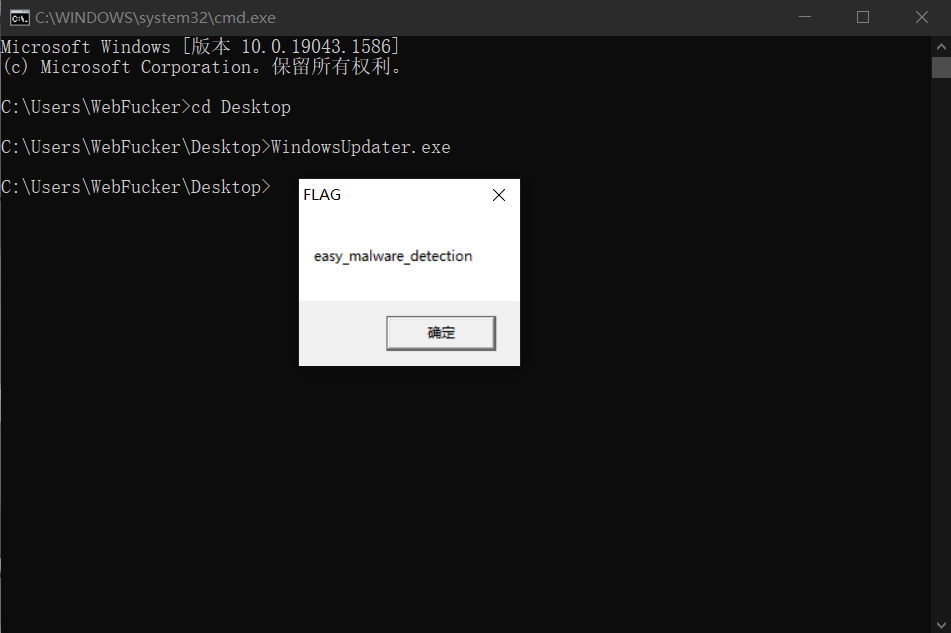
The Whale
Description
Who doesn't love whales? I do, You do, they do.Solution
The memory image is in E01 format, and a Google query tells us that FTK can read it.
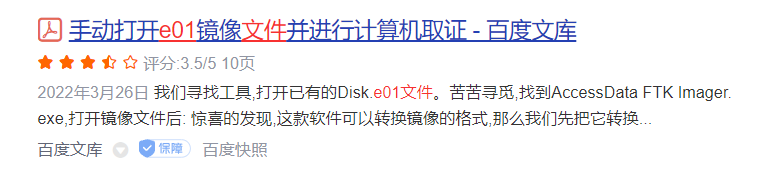
you can see that it is a Windows image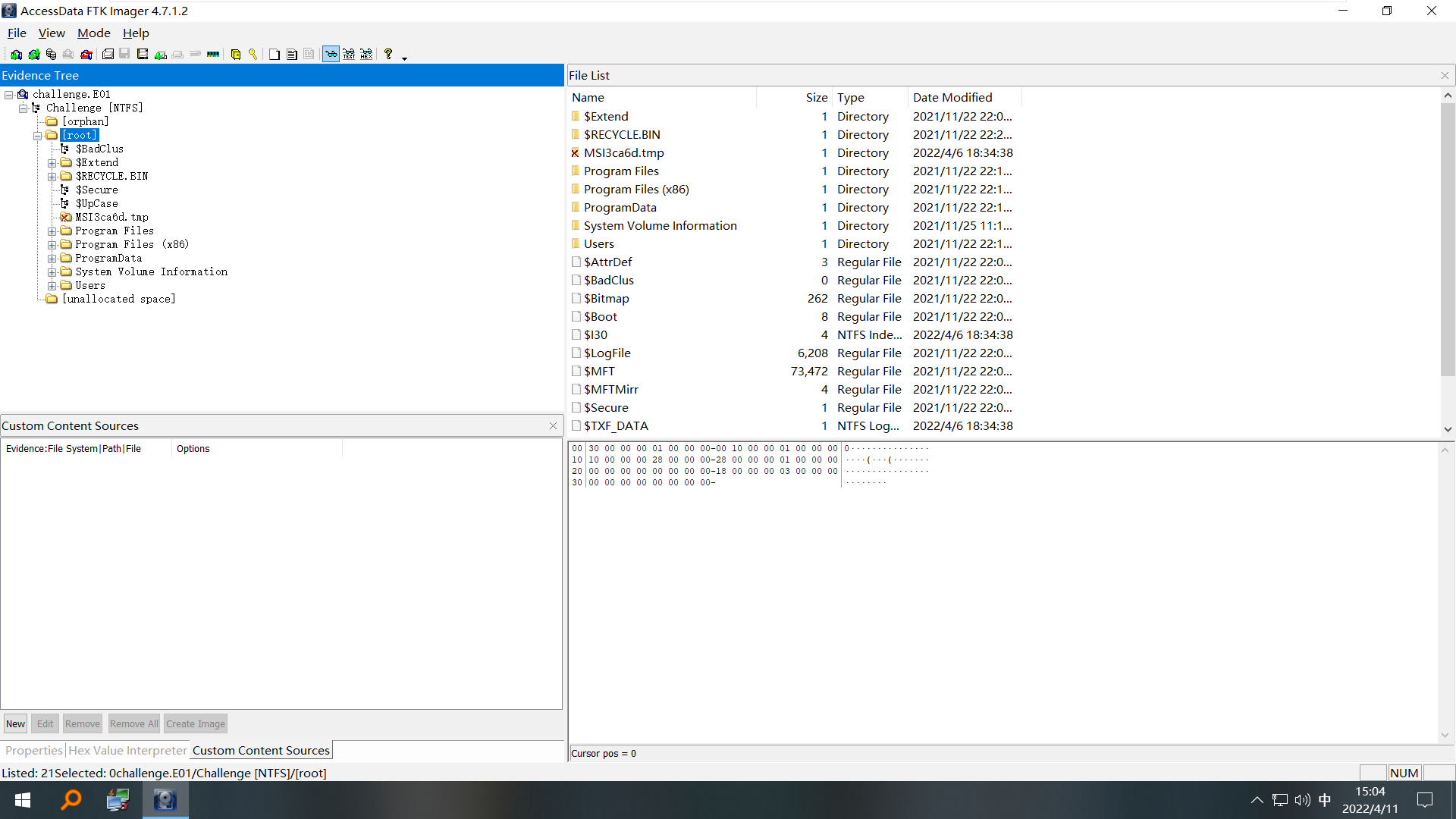
I saw the .docker folder in the Users/semah/ folder and Docker Desktop.Ink in Desktop, and went through the folders and found the WSL subsystem and the suspicious software KeePass Password Safe 2.
WSL: Users/semah/AppData/Local/Packages/CanonicalGroupLimited.Ubuntu20.04onWindows_79rhkplfndgsc/LocalState/rootfs
KeePass Password Safe 2: Users/semah/Documents/Work Content/work.kdbxAnalyzing the user's home/semahba/.bash_history in WSL's Ubuntu system, I found two actions related to docker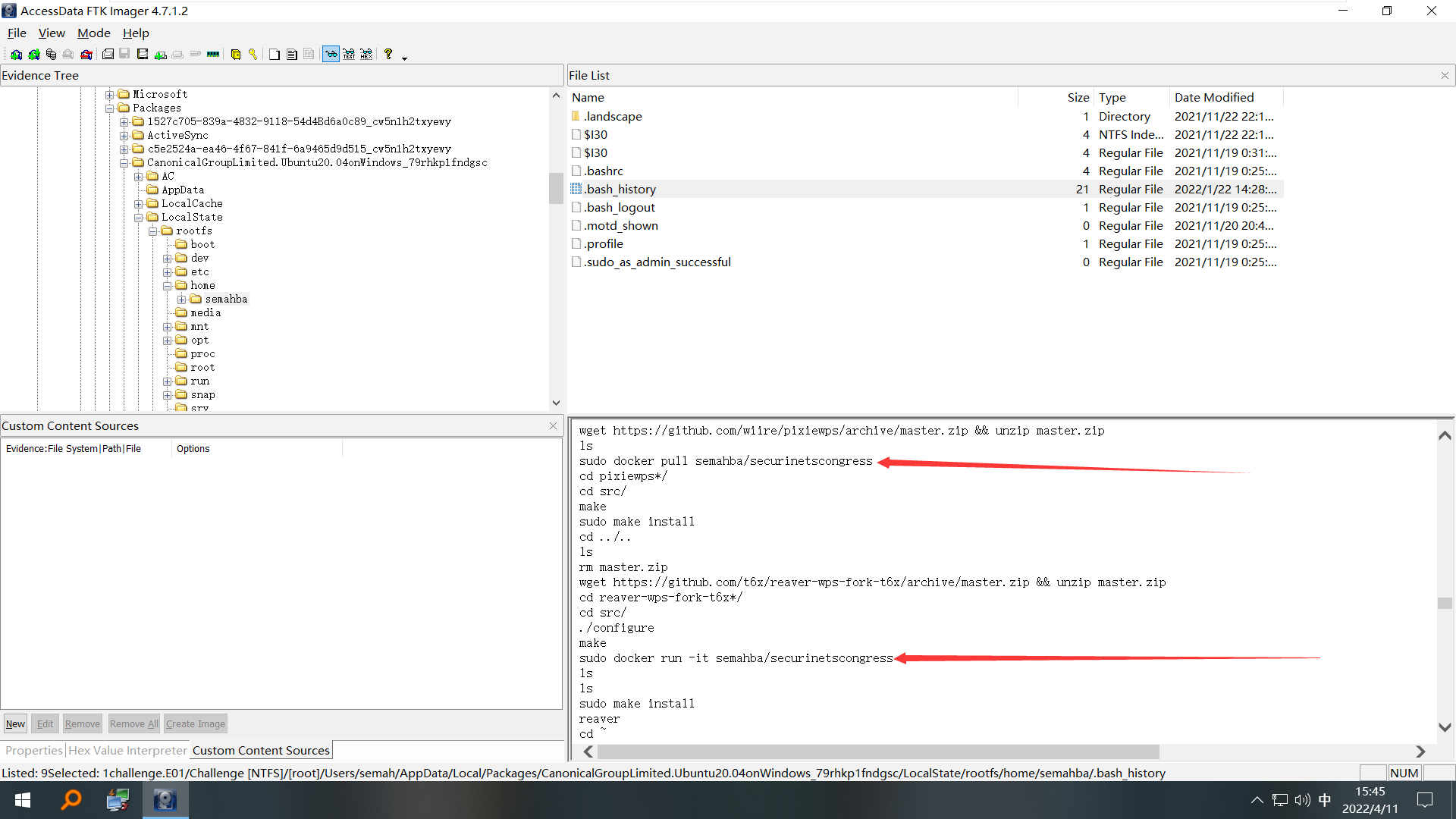
Check IMAGE LAYERS in dockerhub and find two key commands. Local up docker, dump the secret.enc file.
/bin/sh -c echo -n $(curl -s https://pastebin.com/raw/mtRhi3tv) | openssl enc -aes-256-cbc -iter 10 -pass pass:$(cat /var/securinetsCongress/5f4dcc3b5aa765d61d8327deb882cf99.txt) -out /var/securinetsCongress/secret.enc
/bin/sh -c rm /var/securinetsCongress/5f4dcc3b5aa765d61d8327deb882cf99.txtdebugfs and other methods are not working, but under the local docker image I found 5f4dcc3b5aa765d61d8327deb882cf99.txt
root@kali:~# find / -name "5f4dcc3b5aa765d61d8327deb882cf99.txt"
/var/lib/docker/overlay2/c33b509c6669343ae5f9daed47d7e5f7f1e88b3113c2208498e2b8a7d776101d/diff/var/securinetsCongress/5f4dcc3b5aa765d61d8327deb882cf99.txt
/var/lib/docker/overlay2/e138f9a7b442ff3d29bc35ee20d62150d4063f15c8498e8a7d027638f7219b07/diff/var/securinetsCongress/5f4dcc3b5aa765d61d8327deb882cf99.txt
root@kali:~# cat /var/lib/docker/overlay2/c33b509c6669343ae5f9daed47d7e5f7f1e88b3113c2208498e2b8a7d776101d/diff/var/securinetsCongress/5f4dcc3b5aa765d61d8327deb882cf99.txt
Lgt6G6T2wZlM3A2o1QkgkE\IvN}]QJ!N9\dxLO/Q
root@kali:~# openssl enc -aes-256-cbc -d -iter 10 -in secret.enc -kfile 5f4dcc3b5aa765d61d8327deb882cf99.txt
Only Employees have access to our sensitive work data. Don't share it! pwd: cvvsBZhRBgjqXefLkMwWThe content says work data easily recalls the KeePass encrypted file work.kdbx, which can be decrypted with pwd to get a password and a URL.
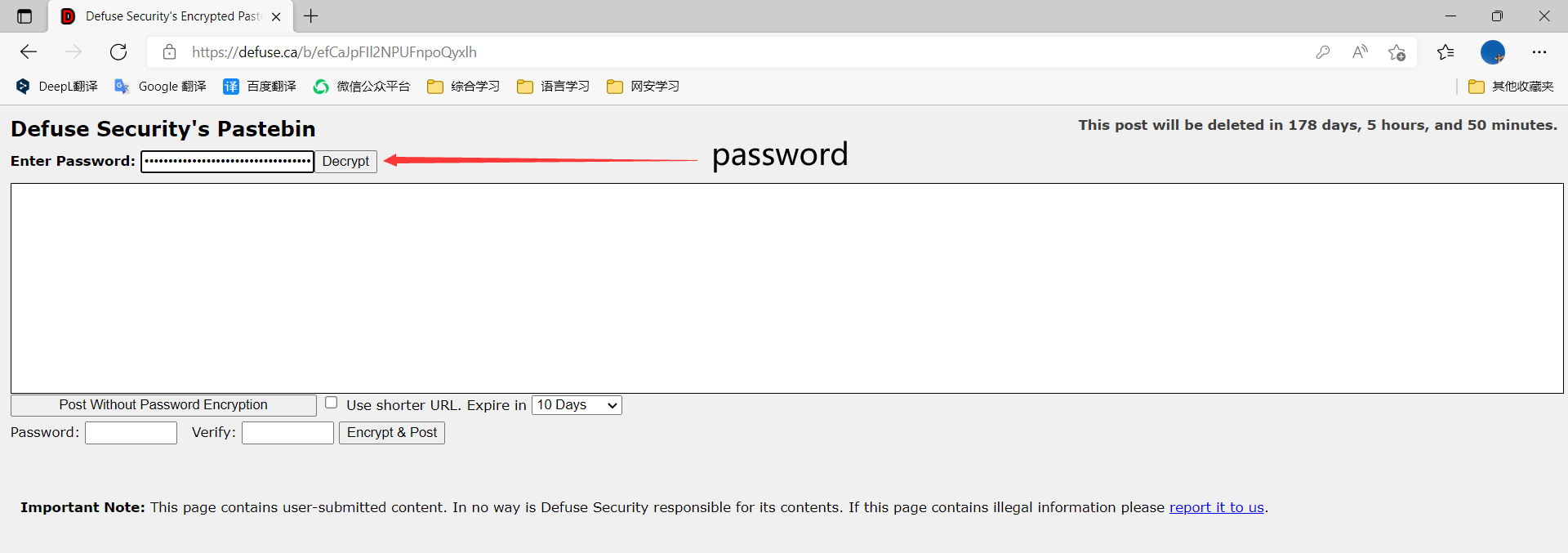
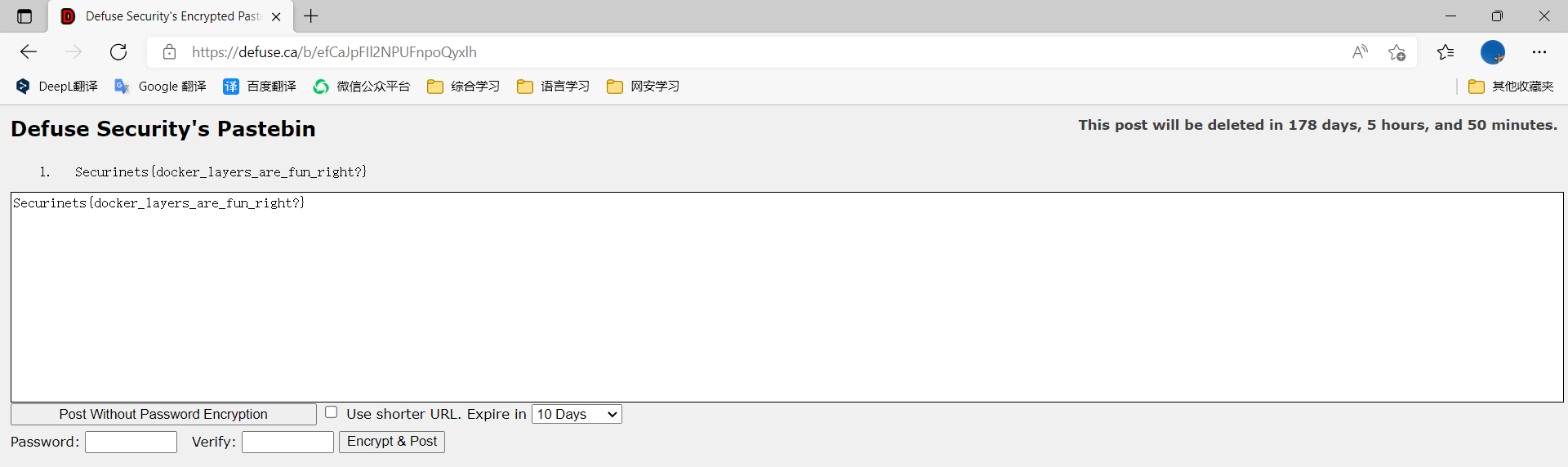
password: Vb0CkhUnRsnObwFA2vBvMjfGEg9ZtSYgB/3RGgQCRGuL5h4RJQcOdTzb/hs/fUP0
URL: https://defuse.ca/b/efCaJpFIl2NPUFnpoQyxlh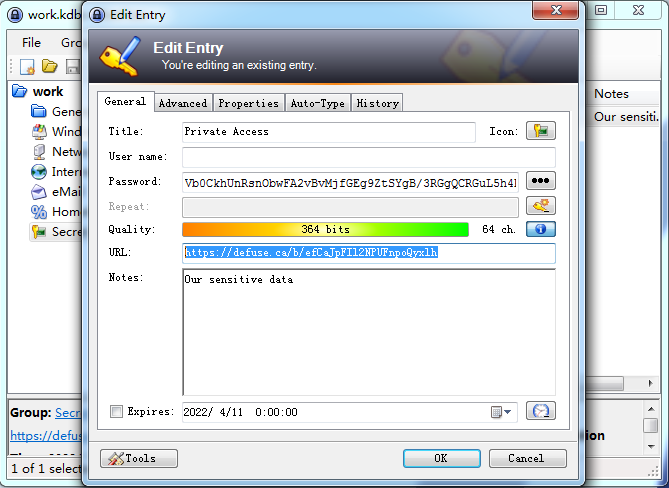
Open the URL and type Password, you can getflag